
The current security tests mainly refer to the security scanning implemented manually or using certain tools and penetration tests. Because penetration tests and security attack need rich experience and skills and special skills are also needed by security scanning and penetration tests by specific tools, only a small amount of professionals can implement security tests. The routine security tests can be implemented through automatic methods with many tools, and also can be integrated into CI, which allows all the developers in the team to discover common security problems in software immediately. As a result, it is not necessary to wait until security experts find problems and work overtime to fix them before the system is brought online.
The automatic security test mainly includes the following parts:
It is very costly to discover security problems by manual review. Besides, with the increase of project codes, difficulty and cost of review will also be higher. Therefore, static code scanning can be used to scan the codes, and various problems can be discovered at the level of static code scanning, including security problems. And automatic scanning tools can incorporate CI, which can undertake automatic scanning along with the CI pipeline to guarantee that codes delivered every day can be checked, and thus prompt feedback can be realized and cost of discovering problems and maintenance can be reduced.
For this P2P project, Fortify can be used to scan all the codes of Android,iOS and Web systems. However, static code scanning tools like Fortify can discover many security vulnerabilities at various levels, so it may cost a long time for assessing these vulnerabilities. If taking the project cost as priority, high risk vulnerabilities can be paid attention to firstly, and vulnerabilities with low priority can be fixed later.
Although static code scanning can be used to discover security problems, security vulnerabilities at system level still may emerge after components are integrated together or after the system is deployed into test environment, such as security problems of XSS and CSRF etc. Therefore, security problems can be discovered by dynamic security scanning applied at this moment in the shortest possible time. There are two types of dynamic security scanning: active scanning and passive scanning.
Active scanning indicates that the address of the system subject to scanning shall be given firstly, the scanning tool accesses the system by some way such as by various known vulnerability models, and vulnerabilities of the system are then predicated based on the response; or various types of random data (fuzz testing) are embedded into access request to implement some simple penetration tests and weak password tests. However, active scanning is not applicable to systems with complex business process. For example, for a payment system which needs logging in and filling a lot of forms, passive scanning shall be applied.
Fundamental principle of passive scanning is to set scanning tool as a proxy server. Functional testing accesses the system through this proxy server, and the scanning tools can intercept all the interactive data and analyze them. Through pattern matching with known security problems, possible security vulnerabilities can be discovered. In order to be integrated into CI more easily during practice, passive scanning is usually used when performing automatic functional testing to realize the continuous security scanning.
Although most of the basic security vulnerabilities can be discovered by automatic scanning tools, such as XSS and CSRF etc. , it cannot discover security vulnerabilities related to business logic, identity authentication and permission validation, but automatic business security functional testing can find them.
In the P2P project, firstly, ZAP and SQLMap can be used to implement passive scanning and SQL injection scanning for Web Service API. Secondly, automatic test on Evil Scenarios obtained from business analysis and threat modeling can be implemented by using Calabash on Android and iOS apps; as for Web apps, Selenium shall be used to edit automatic security tests. Lastly, these automatic security scanning and tests can be embedded into the project assembly line so as to ensure that they can be continuously and automatically performed after the code is submitted.
There are increasing, more and more complex third-party libraries and frameworks of current application dependency, such as SSL, Spring, Rails, Hibernate, .Net and a variety of third-party certification systems. Moreover, a version determined at system development will seldom be updated afterward for a long period due to high cost for version update, i.e. changes in application methods and processes of API of a new library and new framework may lead to large-scale reconstruction of the system. However, versions are updated frequently because new functions are added to those dependencies or that current problems (including security problems) are fixed. Once a security problem of these dependency libraries and frameworks are found, it will probably be posted online, such as CVE, CWE and WooYun, making systems applying those dependencies subjected to many attacks by exploiting those vulnerabilities.
Dependency scanning means scanning over all dependencies (including indirect dependencies) used by the current application and matching them to security vulnerability database published online. If a vulnerability of certain dangerous level (to be self defined) exists in one of the dependencies, a security warning (to prevent CI compiling success, etc.) will be sent to the developer or system administrator, and thus to start corresponding measures to solve the problem, so as to prevent attacks, avoid or reduce losses.
In P2P project, OWASP Dependency Check can be used for scanning over third-party dependency libraries of Android applications and Web server system to see whether there are security vulnerabilities, and then join them into the CI pipeline with a configuration that the CI pipeline will fail once a high-risk vulnerability is detected, to prevent application compiling and building, and give a warning.
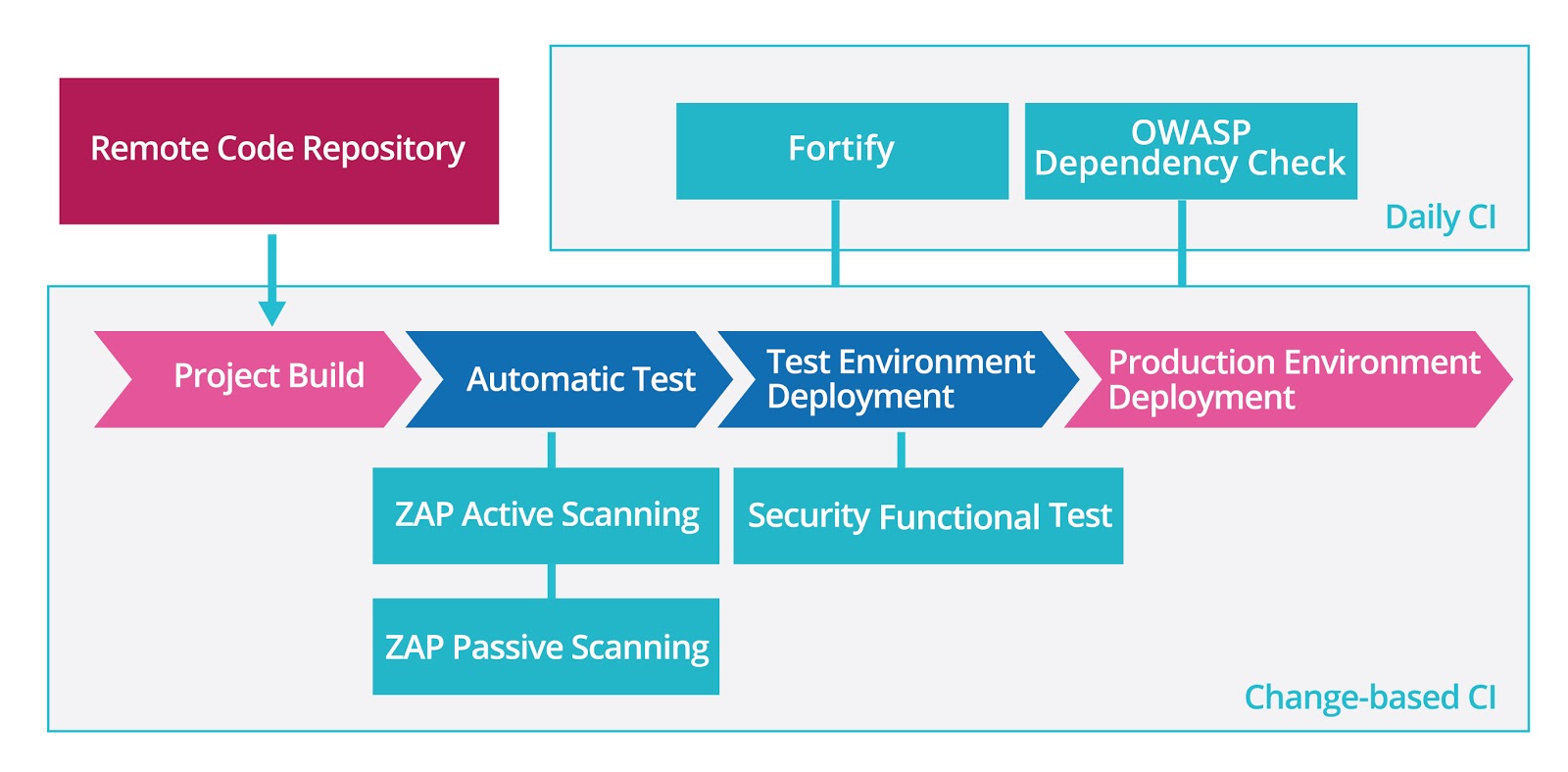
Continuous automatic security scan is applied substituting the manual work of lowest efficiency, to achieve high efficiency. At present, although most security scanning tools cannot detect out all security problems, they are capable of continuously detecting basic security problems of most systems with small input, so as to prevent attacks by most intermediate hackers and almost all junior hackers. However, manual work, such as human review over report on automatic security test, is indispensable for BSI, and security problems, once detected, require manual analysis. Therefore, automatic test in BSI aims to minimize labor cost rather than replace manual work by automation.
Therefore, for system security, security requirement and available resources of the system shall be analyzed at first. In case of limited resources, continuous automatic security scanning shall be conducted at first. For system of high security requirement, manual penetration test shall be adopted when resource condition permits, so as to acquire the highest return on investment (ROI) of security.