
The reason that many companies are facing a dilemma on system security is that relevant security practices have never been launched during the development period of software and therefore more security problems may emerge during business analysis, architecture design or code writing. With regard to how to find and solve the problems, the key is to apply various correct and reasonable security practices during the whole development life cycle.
Procedures of general software development are project planning and evaluation, requirement analysis, architecture design, code implementation, verification test, problem fixing, software delivery, etc. In order to prevent and reduce security issues in the systems, relevant security practices shall be adopted during software development to shorten the feedback period, increase feedback approaches, and to find and resolve security issues sooner and faster.
The mainstream security practices are taken manually by security experts, so the cost is very high and many enterprises cannot undertake comprehensive security control. However, BSI mainly undertakes security practices through the existing roles in the development team. And with a plentiful of automatic security scanning and security test technologies, security problems will be discovered quickly and the true comprehensive security development can be realized. Take the P2P project in the previous chapter as example, implementation approaches of BSI by enterprises will be shown as follows.
At the beginning of the project, in most cases no security practice is implemented. However, as this is just when the development team prepares some spike , it is a good timing to provide security training to the whole team, so as to prepare for demand analysis, development and test in later phases.
Since this P2P project included Web server end, mobile phone application end and server business end, the team contains staff for server end development, mobile phone application end development, Web development, data development and business analysis. With so many staff in various types of positions, if there was one security vulnerability caused by anyone in the system development period and not discovered during testing, it would enter into the production environment. Therefore, security trainings are necessary, including technical security knowledge training such as OWASP TOP10 and Mobile TOP 10 for developers, and security awareness and security business analysis training such as social engineering for business analysts.
Requirement is the soul of software. If there were any faults in requirement analysis, it would be like mental problems for human. No matter how strong the human is, therapies shall be needed continuously. If security problems were omitted, it would be like a child without protection who is gullible and even easy to be abducted. Therefore, security issues must be considered during requirement analysis, for example, if there are security vulnerabilities in business, we shall consider from the point of view of the attacker about how to attack by utilizing this vulnerability. This hypothetical attack scenario is called Evil Scenario.
Certificate authority and financial business rules of this P2P project are very complicated, for example, specific user can only access certain product with authorization, and there are different application processes and use flows for different products. Business personnel shall consider about security vulnerabilities and scenarios of how to utilize this (Evil Scenario), for example, one user try to use the product without authorization or another user try to access information of other users.
Software architecture and design are very important because it determines how the entire software realizes its business structure and data flow. However, the architecture and design of complex business system are also very complicated which cannot be learnt and understood clearly in short term. As a result, it is hard to discover the security vulnerabilities in short term. Because the architecture designer shall be the most familiar with the architecture, security vulnerabilities and threats shall be analyzed during design or before development through methods such as Threat Modeling to feedback the security vulnerabilities immediately and fix the security vulnerabilities at its beginning.
This P2P project included Android, iOS, Web Application, Web Service and the connection with the third-party payment system (including bank system), and therefore, security threats on each level shall be adequately considered during architecture design such as how to guarantee its uniqueness that can prevent deception by hacker while users logging in and accessing through mobile phone, and how to guarantee that verification code will not be stolen and reset while users resetting password. Threat Modeling can be applied to analyzing threats and designing the security architecture, and the general procedures are: firstly, the implementation of STRIDE analysis on each component of the architecture; secondly, risk evaluation through DREAD; and the last, creation of Attack Tree for simulating attack to help developers and testing personnel to understand various possible attacks in the systems.
Code implementation needs close attention on details. The vast codes are written by many developers and different developers have different abilities, and therefore quality of codes may be different, especially security problems may occur during this process. It is hard to guarantee that developers can apply security practice into coding, and both the time-cost and degree of difficulty of manually rechecking the security of codes will be extremely high, and therefore, automatic code scanning can be applied to decrease time-cost and degree of difficulty, and thereby add a feedback loop to discover and solve the security problems in the code immediately. Besides automatic static code scanning, the third-party dependent libraries shall also be used to implement security scanning and real-time monitoring of vulnerabilities, while security management and detection shall be implemented on various tools for development and detection.
In this P2P project, the codes included Java, Objective-C, JavaScript, etc. and many third-party libraries such as Spring, Hibernate, Apache CXF. Facing various programming languages and abundant third-party libraries, comprehensive manual scanning is basically impossible, and tools for automatic scanning are needed. For example, CheckMarx or Fortify can be used to scan the code and then OWASP Dependency Check or Victims can be used to scan the third-party libraries. After integrating these tools into CI, submission for scanning each time or scanning everyday can be implemented. As a result, security problems can be discovered immediately while submitting the codes and thereby be solved quickly.
Verification and test of software functions are the most tedious and very costly, and therefore, except verifying and testing the functions, performance and usability, it is hard to invest more time and labor to implement security test. Commonly, security experts will only conduct a brief security review before the software delivery. However, just as mentioned above, it is hard to discover relevant vulnerability of business. Therefore, during verification and test, the testing personnel shall verify the Evil Scenario and Threat obtained in requirement analysis and architecture design, and make automatic dynamic security scanning and penetration test via security scanning tools to immediately discover security problems in normal verification and test.
Because there are many business sides in this P2P project, test is an intractable process. However, there are many automatic security scanning tools can be used to verify basic security vulnerabilities. As for Web Application and Web Service, ZAP or Burp Suite can be used to implement routine security scanning, and SQLMap can be used for SQL injection scanning. Besides, automatic test framework can be used and automatic business security functional testing can be developed based on Evil Scenario, and in the end, such automatic scanning and tests can be integrated with CI.
After completion of software development including test and when users use the functions, it is also unnoticeable as for security issues. At present, when deploying or using software, many enterprises only have some routine methods for security issues such as purchasing hardware and software firewalls, intrusion detection systems and monitoring systems. However, related vulnerabilities and security of the third-party dependent libraries cannot be detected by these methods. Therefore, system business security training shall be undertaken for operation and maintenance personnel, and real-time detection and alarming of dependent library vulnerabilities shall be implemented.
After the development and delivery of this P2P product, enterprises shall provide business security trainings for operation and maintenance personnel of the server, which includes that the administrator shall not arbitrarily click links in messages or e-mails from users, developers shall help operation and maintenance personnel construct and implement a vulnerability detection and notification system, and that the whole deployment procedure shall be automatic, etc. Releasing of Android and iOS apps shall also be in automatic processes, and manually releasing on the apparatus of one developer shall be avoided.
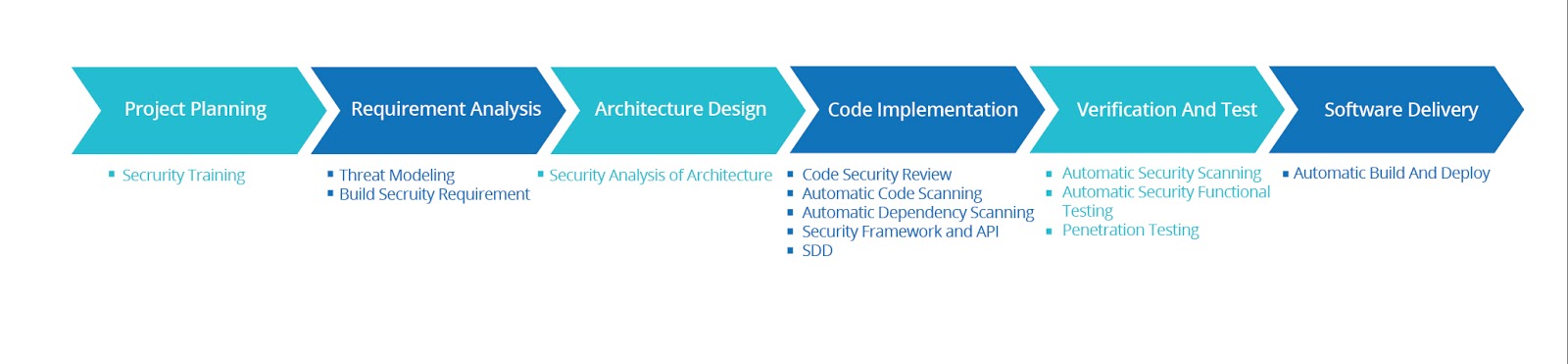
The above mentioned security development procedures can guarantee that there will be no common security problems in this P2P product, which significantly reduces the risk of being attacked by hackers.
BSI is also applicable for the short iterative development, which only needs to add coincident security practices into the iterative development.
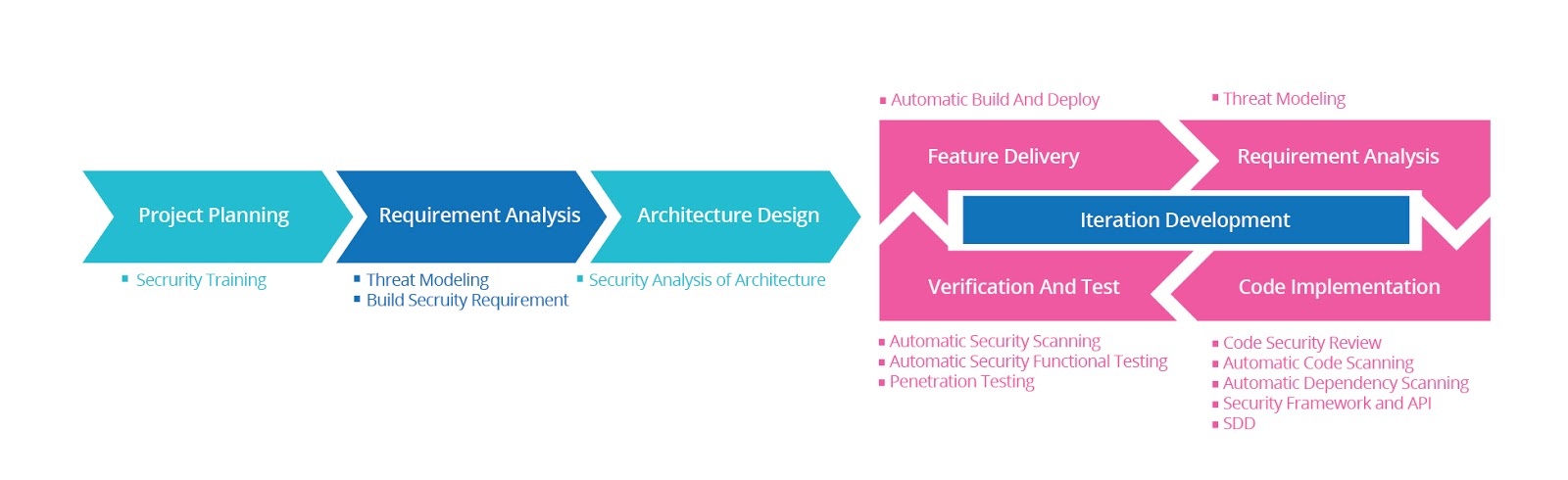
Through adding various security practices, feedback channels of security problems will be increased, feedback period of security problems will be decreased, and therefore, security problems can be fed back immediately for continuous improvement.